|
Risk Managers' Forum
Data, data everywhere
Security breach laws and your responsibility to protect sensitive client data
By Steve Anderson, CIC, and Tim McClendon, CIC, CWCA
The most recent total from the Privacy Rights Clearinghouse's Chronology of Data Breaches (www.privacyrights.org) shows more than a half billion sensitive records breached since 2005. The Chronology lists incidents involving breached consumer information such as personal medical records, credit card numbers and Social Security numbers.
An insurance agency maintains within its offices and systems more private personal information about clients and prospects (personal lines, group and individual health, and commercial lines) than just about any other business type. An agency faces a growing exposure and significant liability if the information in its care is compromised.
There are both federal and state laws that require any organization to take appropriate steps to make sure that private client data is kept private. It is important to note that these regulations include the insurance industry (companies and agencies) under the definition of "financial institution." Don't make the mistake of thinking these apply only to banks. Following is a short description of these laws.
Gramm-Leach-Bliley (GLB) Act. The GLB Act includes two privacy rules—the Financial Privacy Rule and the Safeguards Rule. The Safeguards Rule requires insurance companies to have reasonable policies and procedures for the security of customer information. These policies and procedures must be appropriate to the company's size and complexity, the nature and scope of its activities, and how sensitive its customers' information is.
Health Insurance Portability and Accountability Act (HIPAA). HIPAA's Security Rule requires organizations to ensure the confidentiality, integrity, and availability of all electronic protected health information (ePHI) that is created, received, maintained or transmitted by the company.
HITECH Act of 2009. This is a part of the American Recovery and Reinvestment Act of 2009, aka "the Stimulus Bill," which includes a provision that is intended to be used to increase the use of electronic health records (EHR) by physicians and hospitals. Part of this act requires "reasonable security policies and procedures to protect computerized data containing personal information," as well as nationwide notice in the event of a security breach.
The advent of state laws
In July 2003, California became the first state to enforce a data security breach notification law. Today there are only four states that do not have a state-specific data security law—Kentucky, Mississippi, New Mexico and South Dakota. All other states have since implemented similar laws modeled after the California law.
Every state statute is different but, generally, the following is covered: any personal, non-public information that has not been encrypted and includes a person's first name or initial and last name plus a wide variety of data, including Social Security number, driver's license number, or financial account number in combination with any password that would permit access to a financial account.
The laws state that companies must notify any resident of that state whose unencrypted personal data were, or are reasonably believed to have been, acquired by an unauthorized person that a security breach has taken place. It is important for every agency to fully understand its responsibilities under state laws.
Insurance agencies have a lot to lose in case of data breaches. The most glaring drawback is the time, effort and tremendous amount of money that has to be spent for investigation, corrective action and litigation. Private customer data leakage may also attract heavy fines from regulatory authorities. Breaches and leaks also influence customer perception and lead to their loss of trust. This can result in customers moving their business to another agency.
Therefore, it is of extreme importance that confidential data is identified, protected and destroyed appropriately. It is also vital that the security structure of the organization be taken seriously, because the security of an organization is ultimately only as strong as its weakest link. The rest of this article provides some basic details on the areas to consider while securing information within your agency.
What data needs protection?
The first step in securing your organization from data breaches is to identify the data that needs to be protected. Note that information could be present in physical or computer data form.
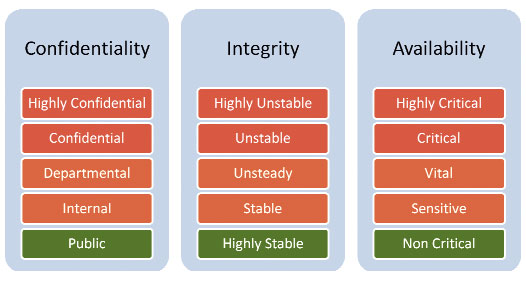
Typically, classification of information can be a combination of their C-I-A criteria: confidentiality, integrity, and availability. Based on an information asset's classification in these three criteria, a security plan can be designed for data that needs to be protected.
For example, in the graphic above, controls to secure data can be determined based on the colored groups. Information that is Highly Confidential, Highly Unstable and Highly Critical falls under the "Highest Level of Security" group and will be fully protected using the strongest set of information security controls. Information that is Public, Highly Stable and Non-Critical falls under the "Lowest Level of Security" group and does not need to have any security controls around it.
Steps to protect client data
Take stock of the personal information you maintain. The first step in protecting data is to have complete control of the data stored or transmitted within the organization. Maintain an inventory of all "Highest Level of Security" information and the software, applications, hardware, services or other assets that interact with this information during storage, transmission or destruction.
Keep only what you need. Data minimization is the practice of eliminating unnecessary information stored by an agency, organization and/or individual for the purpose of decreasing risk of information and, possibly, identity theft. Recommendations for proper data minimization include:
• Don't acquire information unless it is needed. Minimize the number of places where information is stored and retained.
• Purge data once the need for it has expired. For most insurance organizations, the more you know about a client or a prospect, the better. So there may be very little you can do to reduce the scope of this type of data. However, any other data used in the organization should be reviewed from an importance perspective. This will mostly include data that falls under the Public, Highly Stable and Non-Critical classifications, but it could also include other categories. For example, keep only the employee details that are required by law.
• Find out the various places that information is stored. This may include databases, digital documents, physical paper documents, computer printouts, etc., for a single piece of information. Try to reduce any redundancy so that you maintain only original and backup copies as far back as required.
Once data is no longer required, it should be destroyed. This may include insurance policies that have been scrapped more than five years back or details of clients who have died more than seven years ago (data relating to ex-clients may still be maintained as they could still be potential clients for a new product), or financial information from 10 years ago.
Protect the information. As discussed before, data protection depends on their C-I-A criteria. Ideally, all the controls stated below will be applicable to information in the "Highest Level of Security" group. This includes personal customer data. Information that forms part of other groups should be secured by a subset of these controls, based on their classification.
Policies and procedures. Information security policies ensure that a standard level of information security is maintained across the organization. They demonstrate management's resolve to implement controls and checks to secure data. They serve as a reference to follow when new processes and new types of information make their way into the organization.
Procedures contain the steps required to accomplish what the policies aim to achieve. They contain the exact method of implementing information security controls that an organization wishes to follow in accordance with the policies. This top-down method ensures a uniform approach to data protection and thus maximizes its effectiveness.
Access control. Data stored in digital form must be protected at all points of access. The following are some examples of the types of controls that can be implemented for optimized security.
• User account management. User credentials required for access to various information systems should consist of a user ID and password or other credential (such as digital certificates, tokens, etc.) that is unique to an individual.
• Privilege management. Minimum privileges required for every job function and role should be identified based on discussions with the functional teams.
• Password management. User passwords should remain confidential and not shared, posted or otherwise divulged in any manner.
• Monitor access. User activities should be logged by the operating systems, agency management system, applications, other databases and network elements.
• User access policies. A policy should be created, making the user aware of his or her security responsibilities by the acceptable use of systems and infrastructure.
• Network equipment. All network equipment and communication lines should be identified, documented and updated regularly.
• Encryption. Data flowing through public networks has to be securely channeled. Encryption ensures that data is not sabotaged in such cases. Encryption of stored data also protects data when storage devices are stolen.
• Backup and recovery. All application and operating system software, data (including databases), application and operating systems configuration information, hardware configuration information (where applicable) and log files/logs from various systems that need to be backed up should be identified. Backup data should be provided for recovery after appropriate approvals.
• Anti-virus. All possible and feasible measures should be taken to prevent the introduction of viruses and malicious software into information systems.
• Physical security. Physical access to information processing areas and their supporting infrastructure (communications, power, etc.) should be controlled to prevent, detect, and minimize the effects of unintended and unauthorized access to these areas.
• Media handling. An inventory of all the media should be maintained. All movement of material going in and out of premises should be duly authorized and tracked.
• Personnel security. The organization should ensure that personnel at all levels are required to contribute to maintaining an appropriate level of information security.
• Proper disposal. Any information that is of no use to the agency for business purposes should eventually be disposed of.
• Create a plan to respond to a security incident. After a breach, many organizations don't know what to do. If a breach occurs, the ability to respond must be timely. Companies have only about 30 days or less. It is thus essential for an agency to have a sound incident management plan in place.
Insurance coverage available
Implementing all of the controls described above tremendously reduces the risk of a data breach to an organization's data. However, it does not entirely eliminate the possibility. An organization may not be able to implement all controls due to financial or other business reasons. A new virus, an unknown backdoor, an intelligent hacker or a disgruntled employee may find a way to violate an organization's data.
The good news is that liability for losses due to security breaches can be transferred to a third party in the form of an insurance policy. Predictably, though, most insurance agents do not purchase this coverage themselves. They may recommend it to clients, but they forget about their own exposures.
There are currently about 16 companies providing network security and privacy liability coverage for those firms actually engaged in technology business, such as programmers and technicians; but only a few have policies to cover the exposures of day-to-day transactions carried out in offices and on the Internet. In general these policies may cover:
• Privacy and security liability
• Business interruption
• Crisis expenses for restoring lost data
• Customer and/or partner notification costs
• Media or Web content liability for charges of libel, slander, copyright and trademark infringement
• Legal liability and regulatory action expenses
• Identity theft
• Unauthorized disclosure of private information
• Network damage
• Cyber extortion
• Crisis management and cyber investigation
As you recognize the privacy liability risk for your organization (and your clients), you will want to be aware of the wide variety and quality of coverages available and evaluate the coverages available against the ease of purchase and overall price. A good risk management tool for you and your clients is actually found in just completing an application for coverage. A quick look at the underwriting questions will let you or your client know if additional steps should be taken to protect valuable information.
Here are a few of the coverage questions you should be asking:
1. What causes of loss are covered?
2. Are employee acts covered?
3. Is there a limitation on media type?
4. Is there a digitization requirement?
5. Is there a response to regulatory investigation?
6. Is coverage dependent upon the performing of services or can a loss occur spontaneously and be covered?
7. Must identity theft actually occur for the policy to respond?
This issue is not going to go away. The insurance industry, and especially agencies, needs to review its internal data security controls and create a plan for effectively protecting private client data. It also represents an opportunity to create additional revenue by talking to your existing clients about their need for this new coverage.
The authors
Steve Anderson, CIC, has been an insurance agent for more than 30 years. He is editor of The Anderson Agency Report (www.TAAReport.com) and a contributor to many insurance publications. Steve appears frequently as a speaker, helping agents maximize productivity and profits using practical technology. Contact him at: Steve@SteveAnderson.com.
Tim McClendon, CIC, CWCA, has close to 40 years' experience in the insurance industry, including working for a major carrier and starting an insurance agency from scratch. Currently, he is managing partner of Hertel McClendon, LLP, in Fort Worth, Texas. He is a licensed risk manager and a national faculty member of The National Alliance for Insurance Education & Research. Tim has been a member of the adjunct faculty teaching insurance and risk management courses at Texas Christian University (TCU).
For information on The National Alliance's Certified Risk Managers (CRM) program, go to: www.TheNationalAlliance.com.
|