|
 |
 |
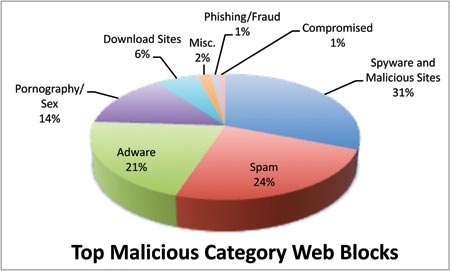
Managing Mobility Safe Web surfing Five tips to use whether you're at your desk or on-the-go By Fred Touchette The Internet is full of useful information that may be widely accessed and available. But when it is used for malevolent purposes, innocent-looking and legitimate Web sites can be hacked and deliberately infected by cybercriminals. These Web sites are loaded with harmful malware that wait for an opportunity to download itself onto visitors' computers. Once the malware has installed itself on a machine, it can be controlled by the cybercriminal who will command it to start collecting personal data, edit and move files, modify e-mail, interfere with applications and programs or lock your computer for ransom. Keyloggers can even monitor your keyboard activities and track your typing patterns such as passwords and credit card numbers. There was a time when the majority of malware traveled by e-mail in the form of Trojanized attachments. While still a promising method of delivery, the majority of today's malware is placed on legitimate Web sites that have been compromised by cybercriminals. As the graph below depicts, the majority of Web blocks are derived from users attempting to access malicious pages—showing the real danger that business and personal networks face if they are without Web security. Even worse, users may believe they are navigating safe Web sites visited numerous times before without realizing that the bad guys took control of the site the night before and are now serving up malware from the same location. Cybercriminals will often utilize a multi-vectored approach in order to lure users to sites where malicious payloads reside. They may do this by delivering a convincing ruse to targets via e-mail and providing a Web link which, when clicked, sends the new victims to the first of what can be multiple compromised Web sites. Some of these sites simply serve as redirects, while others provide exploits that leverage vulnerabilities in popular software such as Java, Adobe Reader, et al. to gain access to machines. Other redirects along the way can provide payloads that help the attacker retain access to the now-compromised machine as well as other components that monitor keystrokes, steal bank account information, browser histories, cookies, etc.
Sometimes it is easy to tell if a machine is infected, while other times computer viruses are specifically designed to remain undetected by both the machines' operators and by anti-virus solutions. Regardless, once malware finds its way onto a computer it is often too late. Bugs go right to work stealing whatever they can find and recruit new hosts into botnet armies that aid in propagation of threats both over the Web and through network shares. The best defense is to utilize a layered security approach and block Web threats as far away from the network as possible. By not allowing a machine to connect with a compromised Web site or portion thereof, the chance of infection drops exponentially. This is especially important in drive-by download situations where there is no other vector to the attack, such as an e-mail or link that can be detected beforehand. Here are five tips to help you securely conduct your daily Web activity from app downloads to bill pay, Web browsing, e-mail checking and more. Check the padlock and the text Before entering sensitive information into a Web site, look for the security padlock symbol. The padlock is one way of checking that a Web site is safe and indicates that the information you submit is secure. Double click the icon. It will display the certificate information for the page you are viewing to guarantee that you are on a safe, secure Web site. Make sure the certificate is current and issued to the same company you are visiting. Don't be fooled by a padlock that appears on the Web page itself because it is possible for a cybercriminal to copy the image. So, double check that the padlock is in the window frame of the browser itself. After validating the padlock, you can also check the text before the Web site name in the address bar. The "https" is another indication that the page you are viewing is secure. Pay attention to the Web address. Check the address and if you click on a link, look to make sure that the address stayed the same. If it has changed, then it has taken you to a fraudulent Web address where cybercriminals can monitor and access your information. Hey! Don't click that The cybercriminals that now take aim at computer users en masse have become experts in social engineering or the art of manipulating people into performing a certain action. Cybercriminals are constantly coming up with new and creative ways to get you to do what they want. In most cases that is to click on a malicious link or response to a malicious e-mail and often leads to financial or identity loss. Never click on a link—or an attachment—from an unsolicited e-mail. Kids and bill pay: Keep 'em separate Do not bank online using the same computer that your children do. A good portion of online scams and spam target today's younger generation of Internet addicts. Chances are that computers accessed by less-discerning youthful users will be infected with malware and viruses. Instead, it is wise to designate a separate PC solely for secure financial transactions. Bundle up Since attackers are attempting to take advantage of you at any angle possible, it is a good idea to take a layered approach when it comes to security. Make sure you are implementing multiple solutions such as a firewall, anti-virus software, e-mail spam filtering and Web filtering. Extend the vigilance to your mobile device Remember, the same dangers that exist on the Web (i.e., black hat SEO poisoning, social media, e-mail and SMS) can also exploit a mobile device. Remain vigilant about all mobile Web surfing activity. Avoid downloading apps from unknown sources and instead seek out official marketplaces. If you are downloading an app from an established marketplace, learn what others are saying first about the app in the review section. Be aware of the permissions an app is asking for during install. Nearly all smartphones are now equipped with WiFi functionality, making them highly vulnerable to attacks. There are various tools available that allow even the least talented hacker to exploit WiFi hotspots and intercept Web traffic. Avoid accessing any password protected site or one where you will give any personal information (i.e., Facebook, Banking, Paypal) when connected to an unsecured WiFi hotspot, such as those in a coffee shop or at the airport. Businesses should seek a Web filtering solution that will guarantee that Web protection and policies remain active in such harsh environments. The author Fred Touchette, CCNA, GSEC, GREM, GPEN, Security+, is a senior security analyst for AppRiver, which provides e-mail and Web security solutions to more than 45,000 corporate customers. He follows spam and malware trends and techniques and develops tactics to fight them.
|
|||
| |||
| ©The Rough Notes Company. No part of this publication may be reproduced, translated, stored in a database or retrieval system, or transmitted in any form by electronic, mechanical, photocopying, recording, or by other means, except as expressly permitted by the publisher. For permission contact Samuel W. Berman. |